Quick Start Demo
This tutorial illustrates Privado ID's main functionalities. It walks through Privado ID's products and tools by presenting a simple POAP use case. POAP stands for Proof of Attendance Protocol, which is used to prove that someone has taken part in a given event.
In this tutorial, you will assume each of the 3 roles required by the Triangle of Trust: the Identity Holder, the Issuer, and the Verifier. You will:
- Set up a Privado ID wallet
- Issue the POAP credential
- Fetch the newly created credential
- Verify the ID holder credential
Set up a Privado ID wallet
To store verifiable credentials, the Identity Holder (the individual receiving the credential) needs a compatible wallet. Here, we’ll use the Privado ID Wallet, which supports both Mobile and Web-based access.
You may use any Privado ID compatible wallet. Our Ecosystem page lists all supported wallets.
To get started with the Privado ID Wallet, either visit the Privado ID Web Wallet in your browser or download the Mobile App and create an Identity.
- Web Wallet
- Mobile Wallet
The Privado ID Web Wallet is a Web-based identity wallet. It is a reference implementation built using our JS SDK. Learn more about the Web Wallet.
Privado ID Wallet App is an implementation of the Wallet SDK, as a way of showcasing its possibilities. Learn more about the Molbile Wallet.
Issue the POAP credential
You will now take the role of an Issuer, in this example, the private institution/trusted entity that held the event and creates a POAP. The Issuer is responsible for both creating the credential and sending it to the Identity Holder.
We will use the Issuer Node UI Demo environment to manage credentials. This environment enables an Issuer to create and manage identities and credentials, generate connections, and manage schemas.
When an Issuer releases a new credential type, they create a schema representation of the credential. This comprises a set of JSON files that gather all the credential's attributes.
Learn how to set up your own Issuer environment by deploying an Issuer node.
To simplify this demo issuance, we provide an existing credential schema with schema type POAP01:
- JSON schema URL
- JSON-LD context URL
ipfs://QmTSwnuCB9grYMB2z5EKXDagfChurK5MiMCS6efrRbsyVX
View this credential's data using an online gateway.
ipfs://QmdH1Vu79p2NcZLFbHxzJnLuUHJiMZnBeT7SNpLaqK7k9X
View this credential's data using an online gateway.
The schema used in this demo was built using the Privado ID Schema Builder and is available on the Privado ID Schema Explorer. Learn more about creating new schemas from the Schema Builder UI guide.
Generate the credential
With the new schema in hand, the Issuer can generate a credential.
Navigate to the Issuer Node UI testing environment.
dangerOnly use this publicly available Issuer Node for testing purposes. Do not submit personal or sensitive data. All data is deleted every 48 hours.
Next, import the schema.
2.1 Click on Import Schema and paste the schema's IPFS address
ipfs://QmTSwnuCB9grYMB2z5EKXDagfChurK5MiMCS6efrRbsyVX: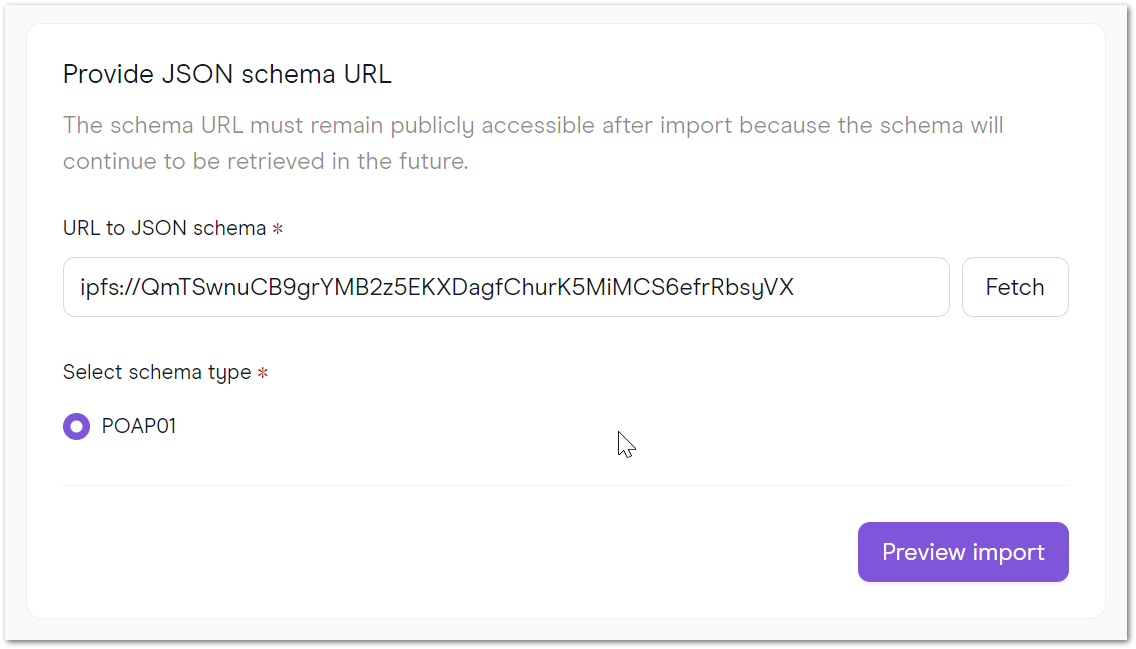
2.2 Preview the schema and then Import it.
Next, click on Issue Credential in the top right-hand corner. Choose Credential Link on the next page and your schema on the dropdown menu ("POAP01", in our case). For this credential, we are providing a proof of attendance at an event in Paris:
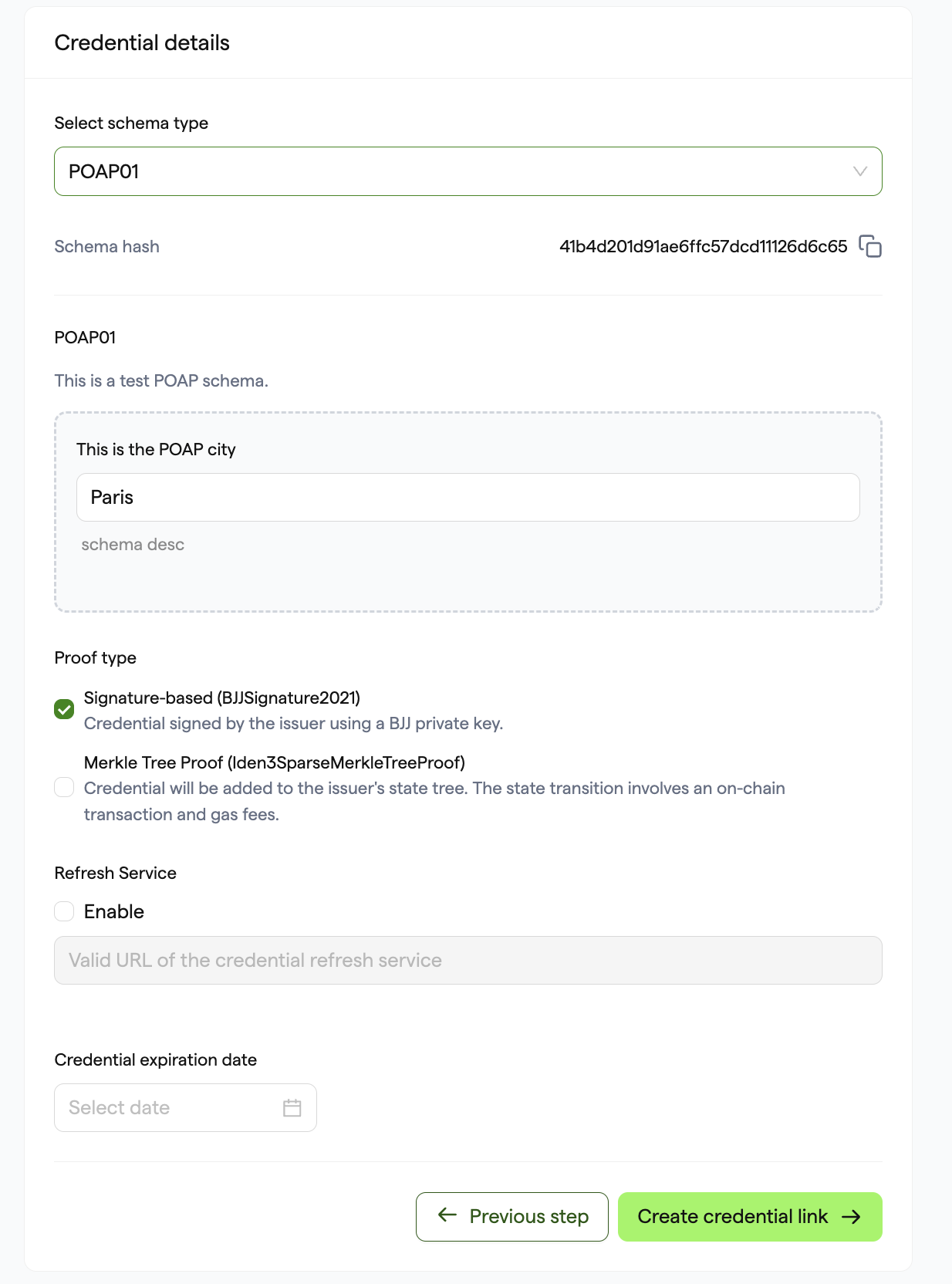
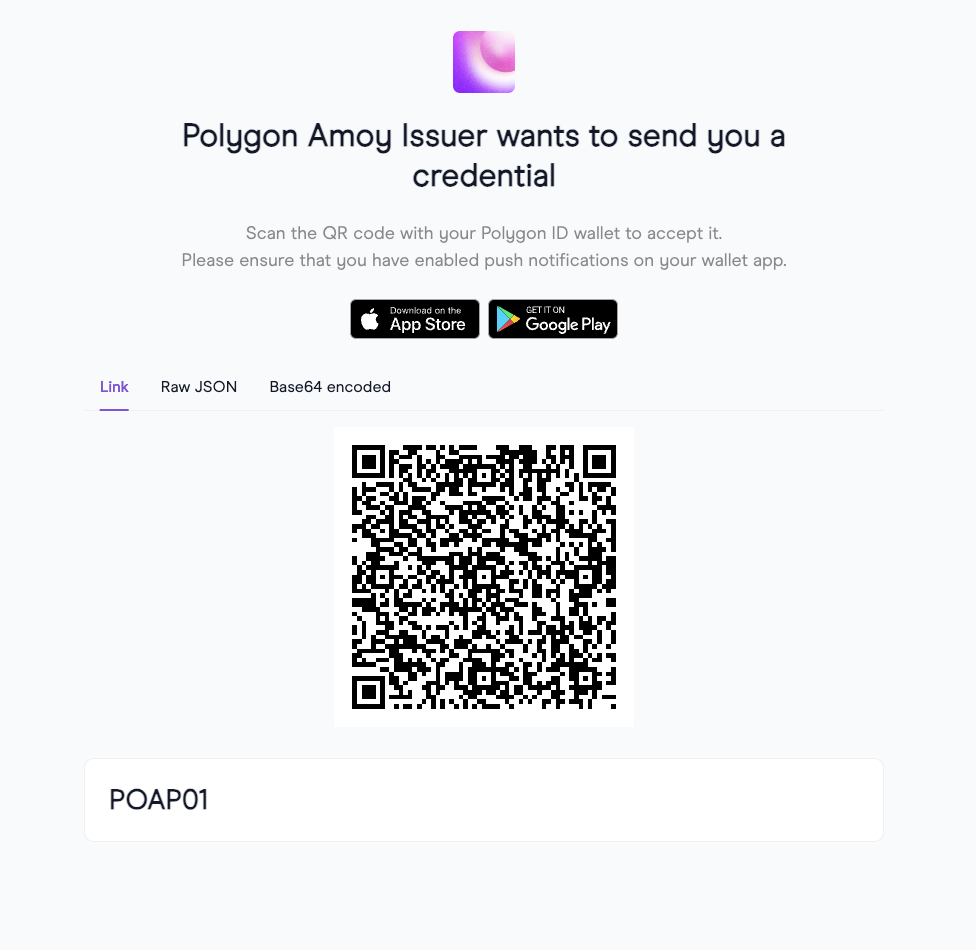
Click on Create Credential Link to be presented with links and a QR code configured for these links to claim the credential. The QR code can be scanned directly with supporting mobile apps, e.g. the Privado Mobile Wallet app.
infoTwo link types are created to provide access to the credential:
- Mobile Wallet apps such as the Privado ID Mobile App and other supported mobile wallets support Deep Link
- The Privado ID Web Wallet and other Mobile Wallet apps support the Universal Link
Fetch the newly created credential
Next, you will take the second role in this tutorial: the ID Holder. You can either use the Web Wallet in the browser or the Mobile Wallet to accept the credential via the link or the QR code generated by the Issuer in the previous step.
To sync the identity and its associated credentials between the Privado ID Web Wallet and the Privado ID Mobile Wallet, the user must log in with the same crypto wallet account on both platforms. Once you claim a credential on one platform, it will then be visible on the other.
To fetch the credential:
- Web Wallet
- Mobile Wallet
- Click the Universal link, which will take you to the Web Wallet. Click Sign In and connect your crypto wallet such as MetaMask. Click Add to my wallet. This should add the credential to your wallet.
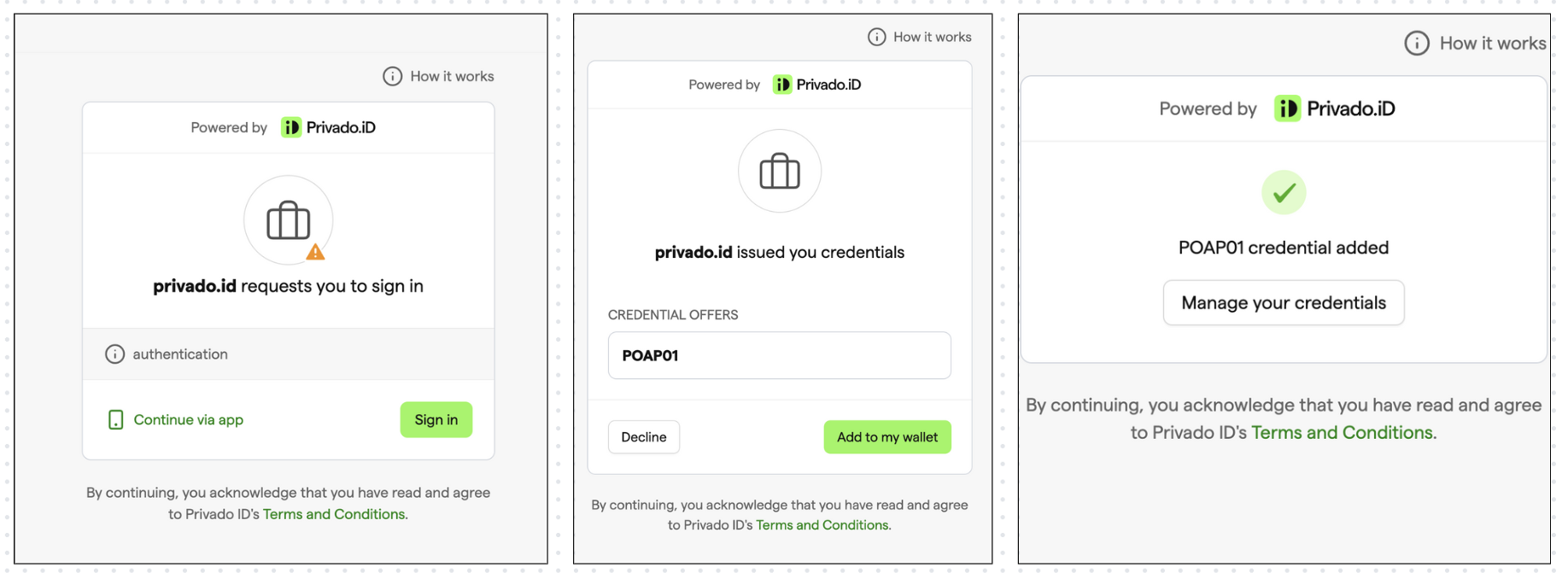
- Scan the QR code. Click Sign In. This should authenticate and add the credential to the Wallet.
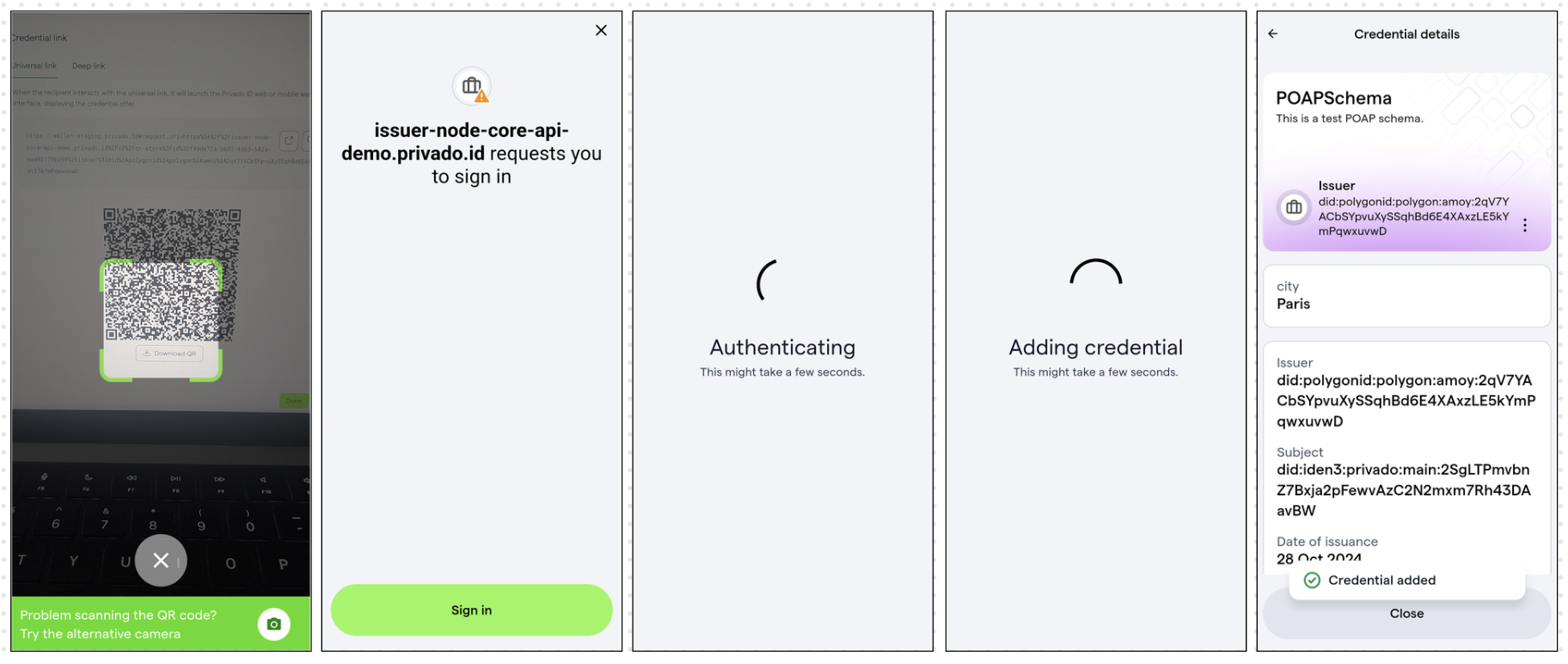
- Click on Manage your credentials to view and manage the credential in the Wallet.
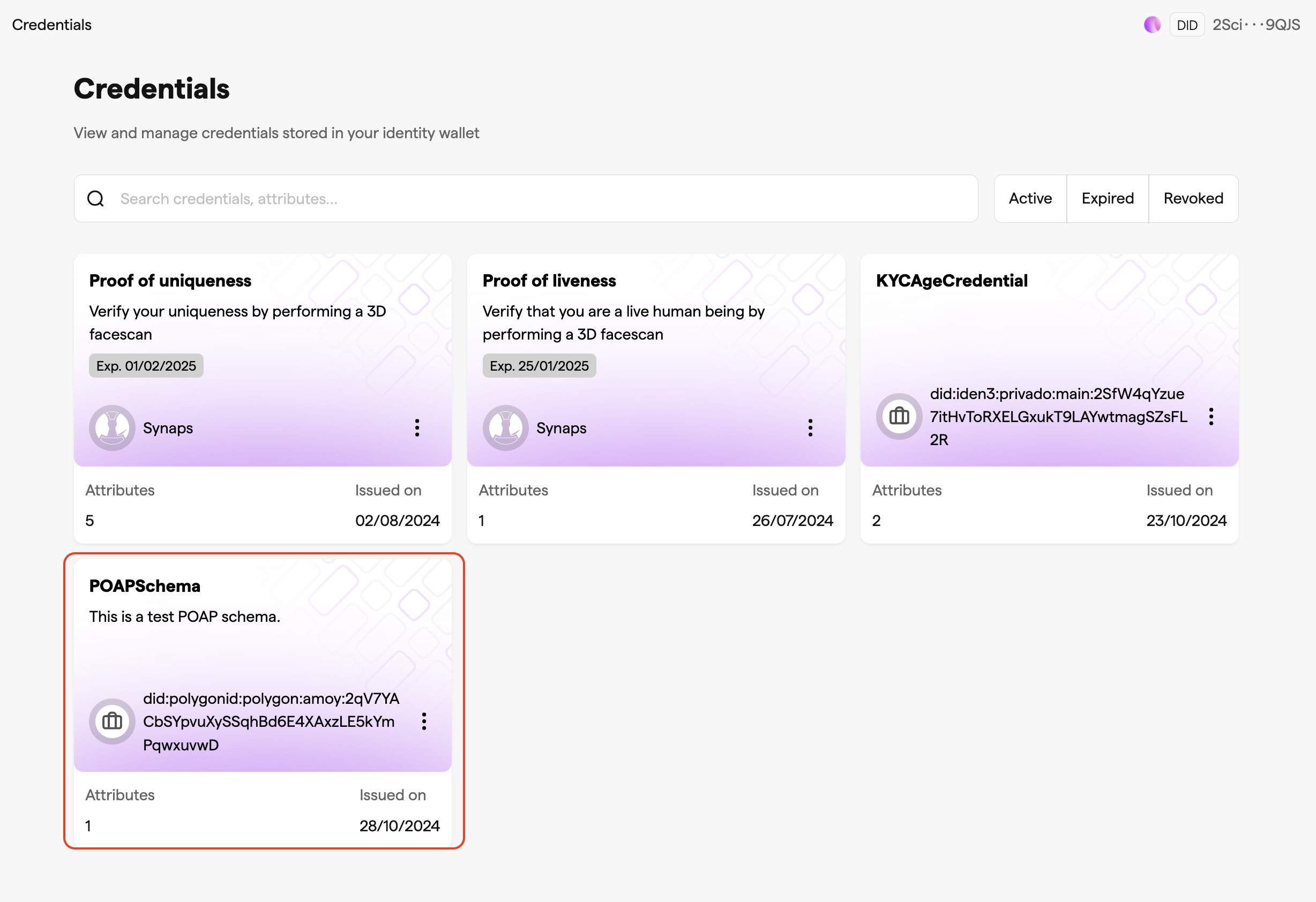
Verify the ID holder credential
Next, you will take the third role in this tutorial: the Verifier. This might be an organization that needs to verify some details of a person's credentials. In our use case, this organization wants to verify whether the Identity Holder actually attended our made-up Paris event.
To verify the credential:
- Visit the Query Builder website. The Query Builder is a tool designed to simplify the creation of verification queries.
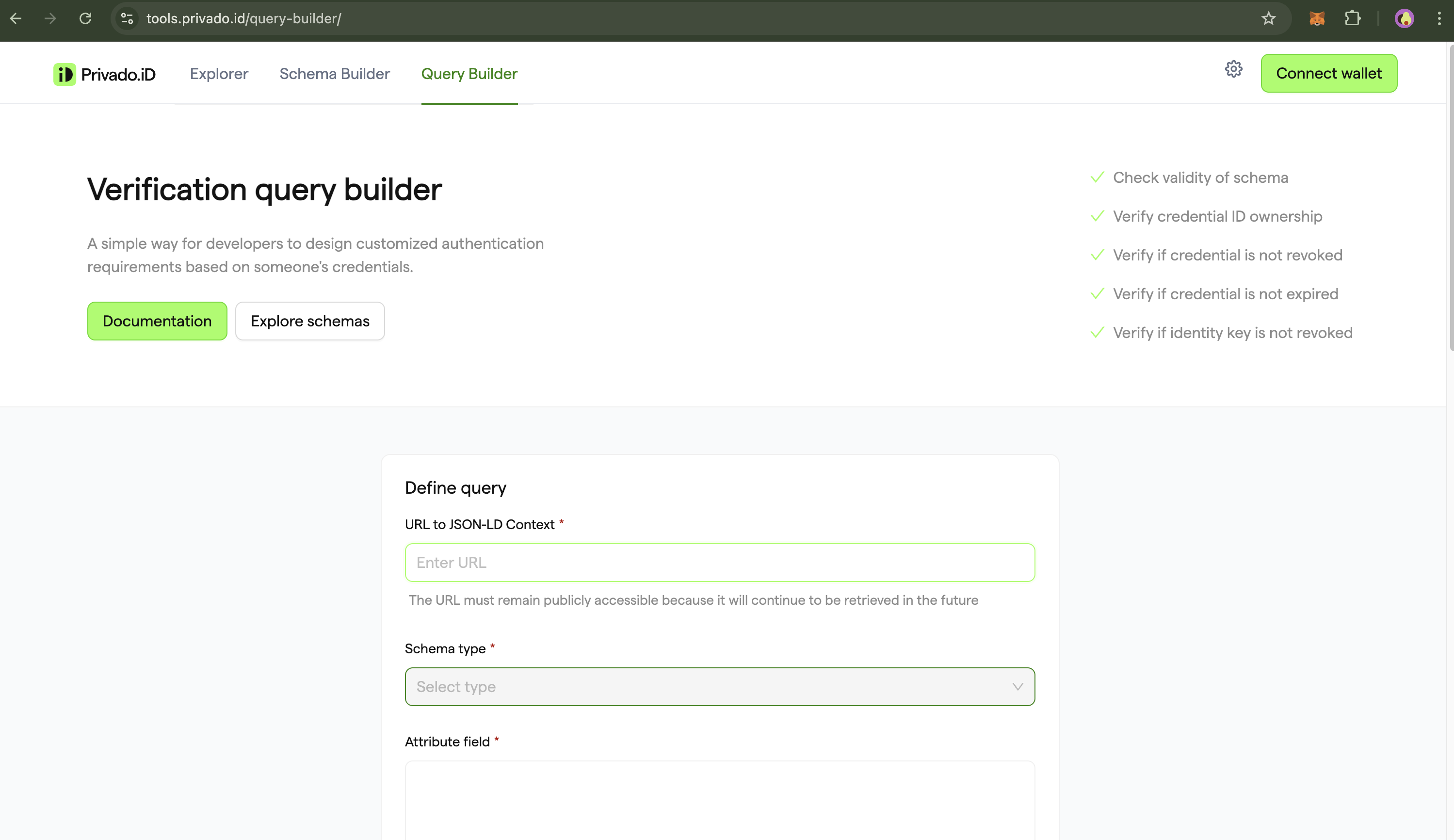
- Define the query. We will use the existing JSON-LD URL:
ipfs://QmdH1Vu79p2NcZLFbHxzJnLuUHJiMZnBeT7SNpLaqK7k9X. The query should look like this:
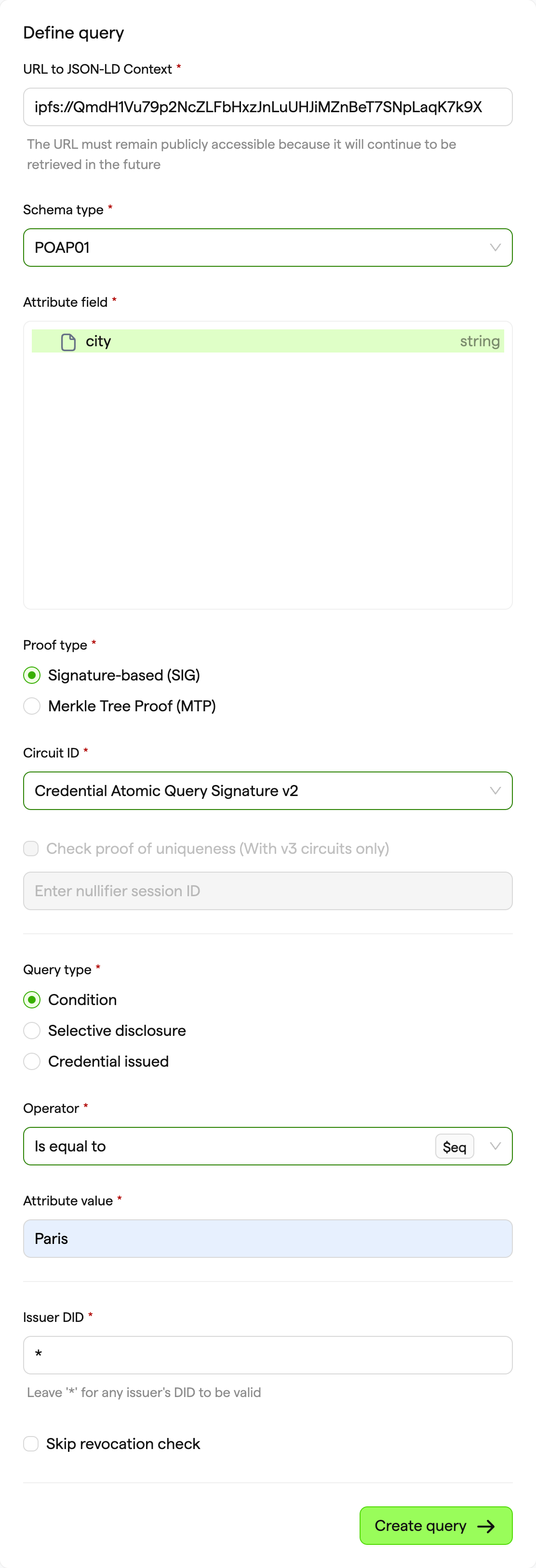
- Click Create Query. Now click the Test query button which will take you to the Privado ID Web Wallet:
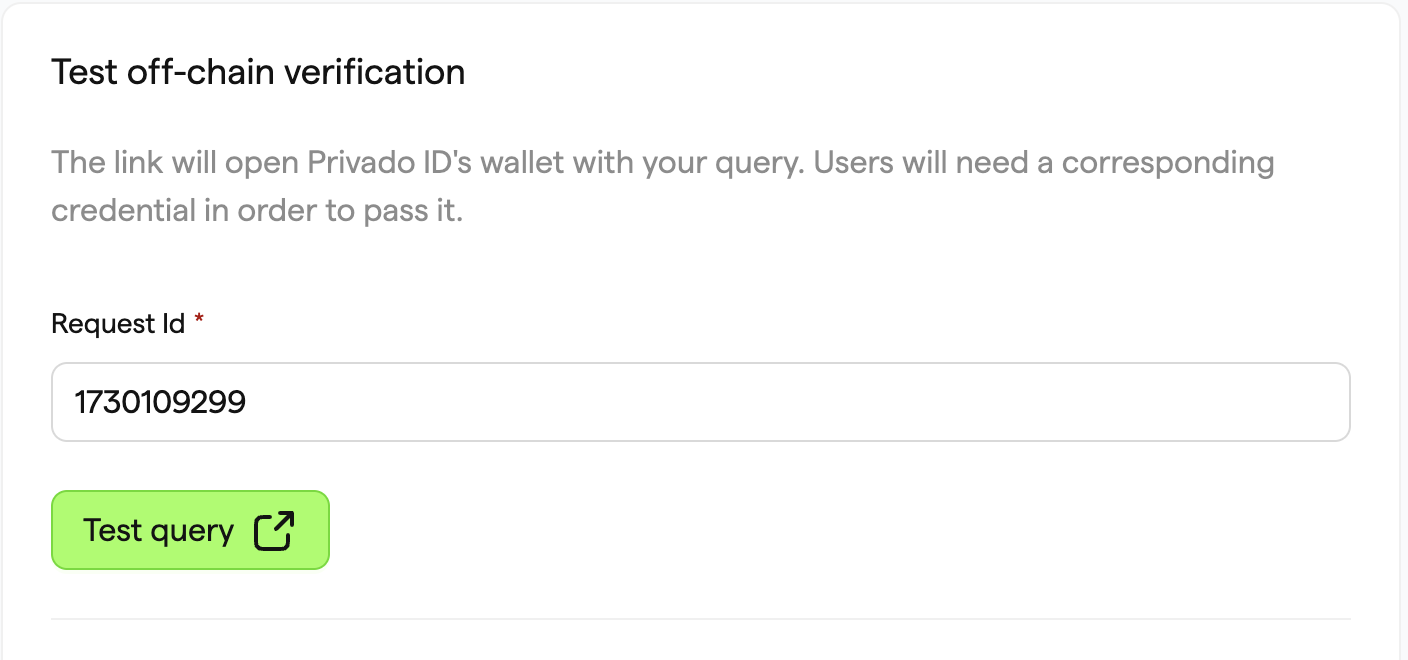
- Click Sign in and connect your crypto wallet. As you have already claimed the credential, it shows as 'claimed'. Click Verify, to initiate the process of generating the proof.
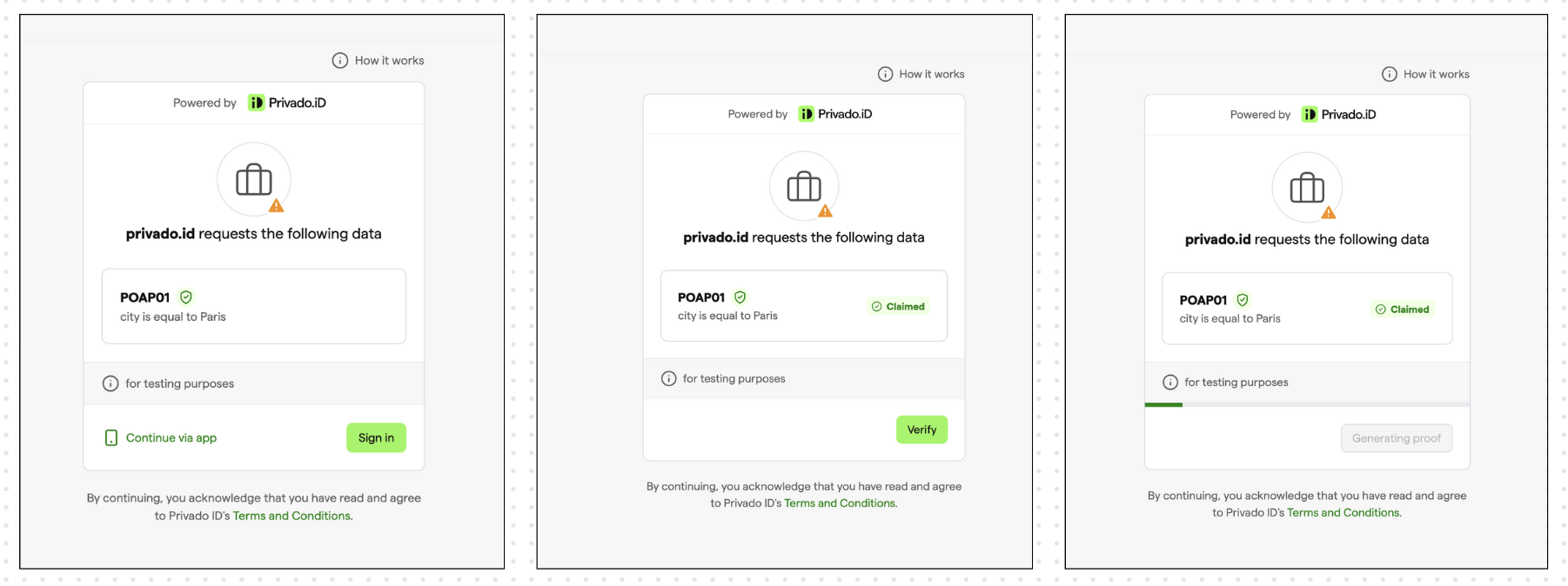
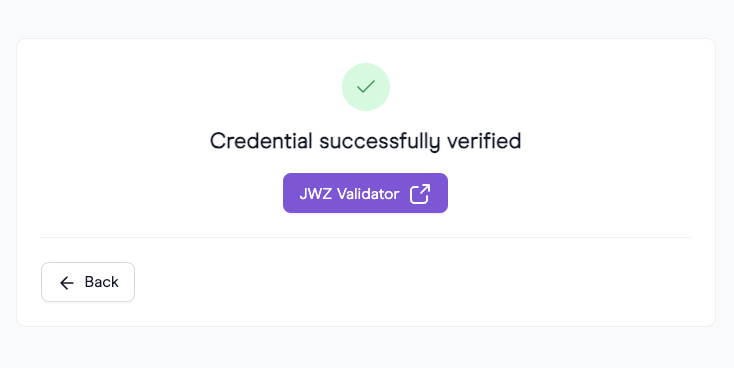
- Finally, the proof is generated and sent to the Verifier. The Verifier will then check the revocation status and any additional information to validate the proof. You will receive the following response on the Query Builder website:
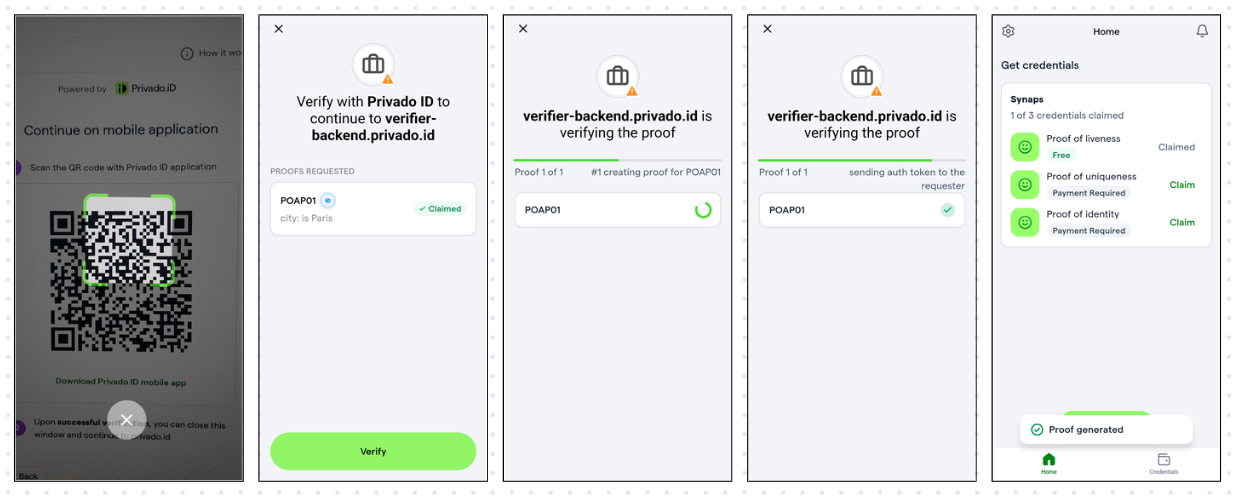
Alternatively, you can also use the Privado ID Wallet app to verify. After Step 3, once you are redirected to Web Wallet, click on Continue via app, this should present a QR code. Open the Privado ID Wallet App and scan the QR code. Click on Verify
This quick-start guide demonstrates Privado ID’s basic functionalities through a POAP use case, covering wallet setup, credential issuance, retrieval, and verification. This example requires the user to participate in all three roles to demonstrate Privado ID's comprehensive suite of Self-Sovereign Identity (SSI) tools for managing decentralized identity and verifiable credentials. In real-world uses cases, a single entity would typically fit just one of these roles.