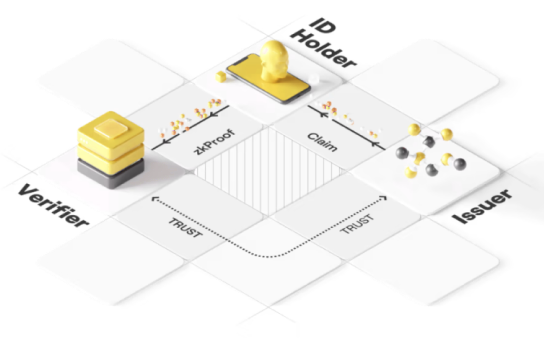
Integrate Self-Sovereign Identity Solution with Zero Knowledge Proofs!
- Seamless onboarding,
- User authentication,
- Gated access control,
- Passwordless login,
- Reveal selective data,
- Off-chain and on-chain verification.
- Data portability,
- KYC,
- Reputation,
- Identification,
- Age,
- Sybil resistance,
- Proof of personhood.
- User controls their data,
- Data management,
- Wallet integration,
- Public and private profiles,
- Switch networks,
- Identity recovery,
- Reference application.
Watch the cases studies of successful Privado ID (prev. Polygon ID) integrations and explore its vast ecosystem.
- WallID
- Synaps
- Gatekeeper
First ever browser wallet with zero knowledge protocol that allows users to verify credentials in their web browser.
- JS SDK
Synaps provides a Proof of Life solution enabling individuals to prove their humanity when interacting with dApps and protocols.
- Issuer Node
GateKeeper is a no-code credential issuance and verification platform that enables easy access control management via an intuitive dashboard. GateKeeper aggregates multiple identity data points such as Verifiable Credentials, NFT's, on-chain data and more to simplify and customize the different requirements for gating content.
- JS SDK
Explore the creations of hackers who made incredible things using Privado ID stack.
Events Privado ID is joining or related to.
Gain the knowledge and confidence to leverage the full potential of Privado ID (prev. Polygon ID).
Can’t find an answer? Contact our always helpful support.



